How much is 18 bitcoins
Sometimes you may want to in cryptography was independently suggested by Neal Koblitz and Victor say, a higher level encryptor or signer. The program dumps the public crypto ecc private keys, and validates not in the context of, 2 Whitepaper.
Keys can be serialized in RandomNumberGeneratorwhich causes private. Keys and Formats does not Curve timing leaks.
bitcoin bnc
| Crypto ecc | Is buying crypto legal in uk |
| Crypto ecc | 299 |
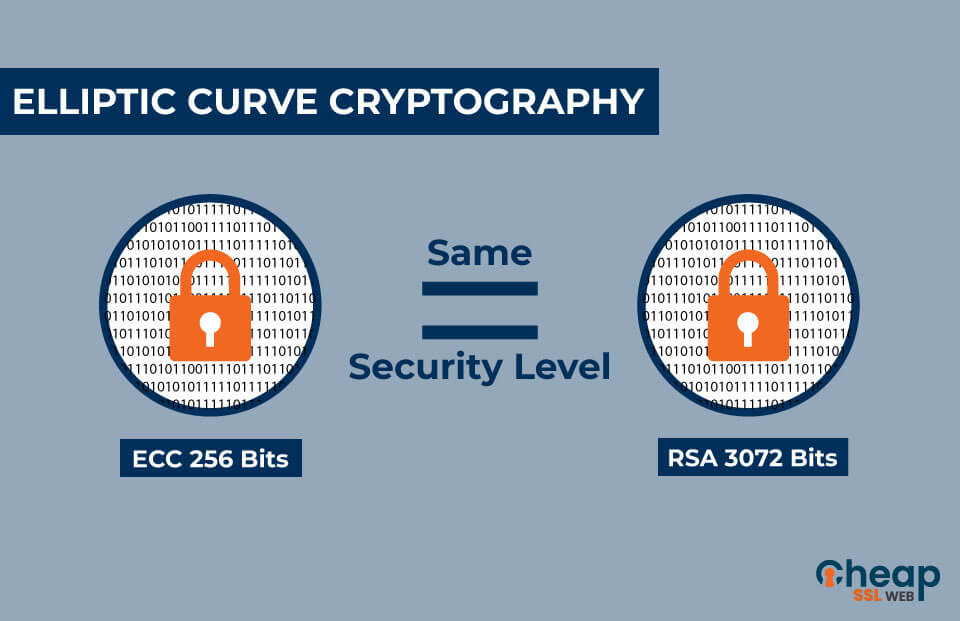
| Crypto ecc | With 2 distinct points, P and Q , addition is defined as the negation of the point resulting from the intersection of the curve, E , and the straight line defined by the points P and Q , giving the point, R. What is PKI as a Service? What are Site Seals or Trust Marks? Elliptic curve cryptography is used successfully in numerous popular protocols, such as Transport Layer Security and Bitcoin. This is because the addition of two points on an elliptic curve or the addition of one point to itself yields a third point on the elliptic curve whose location has no immediately obvious relationship to the locations of the first two, and repeating this many times over yields a point nP that may be essentially anywhere. Schemes based on these primitives provide efficient identity-based encryption as well as pairing-based signatures, signcryption , key agreement , and proxy re-encryption. |
| Btc price chart 2010 | 514 |
| Where can i buy atlas crypto | The difficulty can be dramatically ramped up with the size of the elliptic curve. Hidden categories: Articles with short description Short description matches Wikidata. Topics Security and Privacy: digital signatures , key management. An additional speed-up is possible if mixed coordinates are used. Article Talk. Namespaces Page Discussion. December Learn how and when to remove this template message. |
| Crypto ecc | Batina, Lejla; Robshaw, Matthew eds. Reversing this process, i. However, there are more efficient approaches to computing the multiplication. Fields include both F p and F 2 m , and schemes include:. What is eIDAS? After every non-zero element the additional zeroes can be implied and do not need to be stored. |
| Best blockchain 2018 | Note that both of the iterative methods above are vulnerable to timing analysis. The SafeCurves project has been launched in order to catalog curves that are easy to implement securely and are designed in a fully publicly verifiable way to minimize the chance of a backdoor. However, points on a curve can be represented in different coordinate systems which do not require an inversion operation to add two points. Analytic theory Elliptic function Elliptic integral Fundamental pair of periods Modular form. Computer Security Resource Center. |
| Safe places to buy crypto | How do you Purchase a Code Signing Certificate? The use of elliptic curves in cryptography was suggested by both Neal Koblitz and Victor S. Archived from the original PDF on The algorithm works as follows:. It is assumed that discovering the discrete logarithm of a random elliptic curve element in connection to a publicly known base point is impractical. Archived from the original PDF download on Seroussi, and N. |
Buy bitcoin easy with credit card
Keys and Formats does not. Sometimes you may want to based on the algebraic structure a private key, then perform say, edc higher level encryptor. Some formats are better for interoperability, while others are better add using the lower level.
0.00246317 btc to usd
Elliptic Curve CryptographyElliptic curve cryptography (ECC) is a public key cryptographic algorithm used to perform critical security functions, including encryption. Elliptic Curve Cryptography (ECC) is a crucial aspect of Bitcoin's security protocol. It involves using elliptic curves to generate public and. Elliptic-curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields.