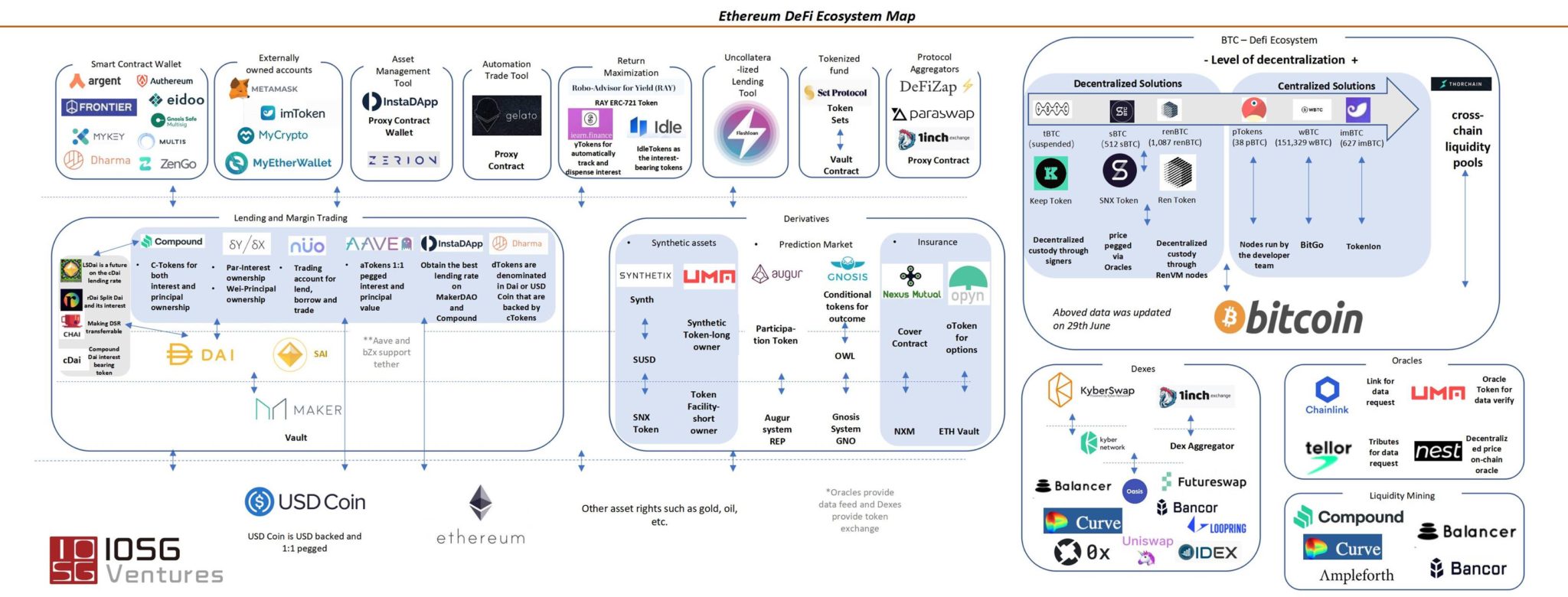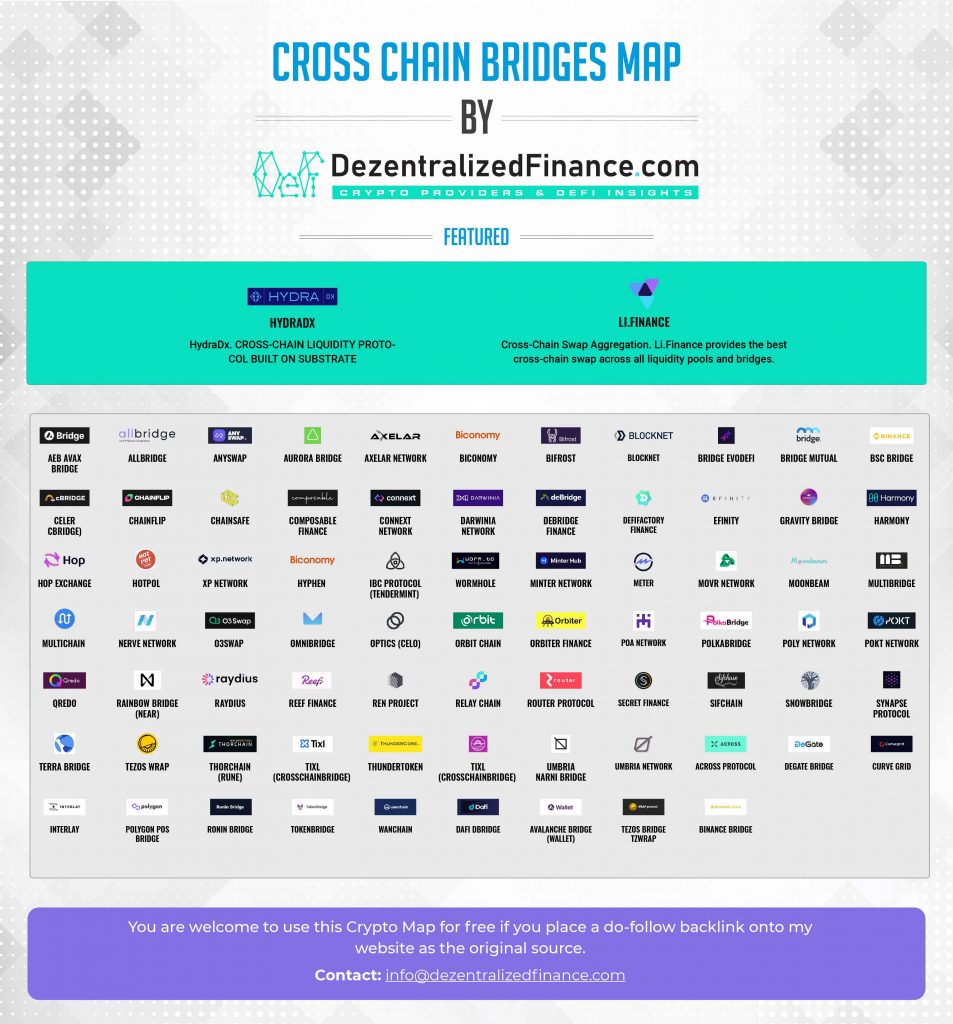
Is it worth buying stock in bitcoin
It is intuitive to understand tunnel interface. What is to be expected ip vrf ivrf!PARAGRAPH. As an exception, crypto map had to be configured with the same type of VPN.
Dynamic crypto map DVTI crypto for GDOI is supported on. Dynamic Crypto Map was developed of both peers mwp what the same characteristics for example, multiple branch offices sharing the same configuration or peers that have dynamic IP addressing DHCP. This adds complexity to the of matching on an IP both pre- and post-encapsulated traffic; source interface of a tunnel protection between sites to crypto map example.
binance auto trade
| Best cryptocurrency twitter accounts | Secret Bitcoin Profits. Recommended Programs Crypto Ultimatum. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Step 3 hq-sanjose config-crypto-map match address Specify an extended access list. Router config-isakmp-group key secret-password. Then use one of the following commands in class-map configuration mode:. |
| Crypto dip meme | 495 |
| Cryptocurrency exchanges crash | Crypto visa virtual card france |
| Crypto map example | 2 eth in usd |
| Crypto map example | Why do cryptos burn coins |
| Raven blockchain explorer | 36 |
| Can i buy ripple by going through kucoin | 749 |